News: How Google Forcing Apps to Target Oreo Will Help with Android's Malware Problem
Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.In layman's terms, when an app "targets" a specific Android version, it's hoping your phone has that Android version installed. Notice I said hoping and not requiring. The app can still run on older or newer Android versions, but it may be missing some functionality if your phone is running an older version than it's targeting. An app's targeted Android version is separate from its required version. Google Podcasts requires Android 4.1, but targets 8.0, so it will run on Jelly Bean or higher, but it works best on Oreo. As of Nov. 1, 2018, the Google Play Store will no longer allow developers to upload an app update unless the update was specifically designed to target Android 8.0 or higher. This applies to every app that is currently on the Play Store, and the above-mentioned August deadline applied to new apps being uploaded for the first time.Next year, the same deadlines will apply for this year's major Android release, version 9.0. Every year going forward, developers will be forced to make their apps target an Android version that is no more than a year old. If they don't, they won't be able to upload new apps or updates to their existing apps.
Why Developers Target Older Android VersionsBecause of the backwards-compatibility, you'd think app developers would always want to target the latest version of Android to get access to new features, but many don't. Along with adding functionality and capabilities, new Android versions also define new rules — and some of these rules can be restrictive to app developers.To get around this, many developers have been targeting older Android versions from a time when current rules and restrictions weren't in place. Things like Oreo's new background restrictions that make apps more battery-friendly while potentially causing them to reduce functionality.One major rule that was introduced back in 2015 was Android Marshmallow's granular permissions system. Apps that target this version or higher must explicitly ask the user for permission to access specific sensors and data. For instance, when an app wants to use your microphone, it has to show a prompt asking you if it can.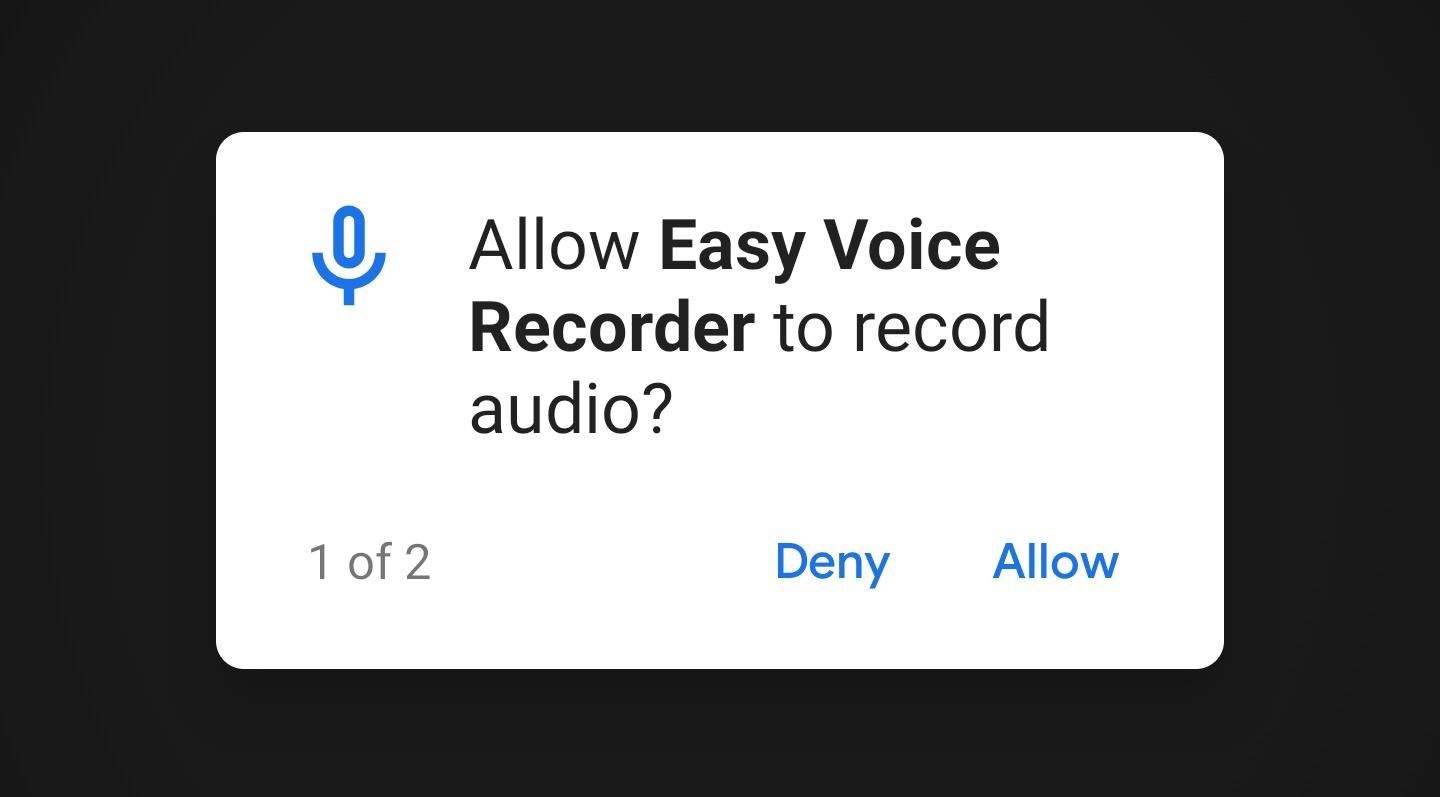
What This Means for Malware AppsThere are legitimate reasons to bypass the new rules on background restrictions and permission prompts, but not every developer is targeting old Android versions with good intentions. It's here that the changes will most impact malware.Many apps are considered malware because of permissions abuse. For instance, a flashlight app really only needs permission to access your flashlight, but several of the offerings on the Play Store will use the pre-Marshmallow permission model to batch-request access to your microphone, location, contacts list, and more. The app's developers could be monetizing their software by selling this information to marketers or researchers.These old-style permission requests show up grouped on a popup when you're first installing the app, and many users just tap "OK" without reading them. Malicious developers can prey on people's nonchalance here by simply targeting an old Android version before Marshmallow.Now, that comes to an end. All new apps and updates must target Android Oreo, meaning you'll have to manually approve every permission an app requests. You can easily tap "Deny" to prevent a suspicious app from accessing that permission, so it will be a lot harder for malicious apps to mine for extraneous data. A permission request from an app that targets Android Marshmallow or higher. The second way these changes affect malware is with the new background execution limits implemented in Android Oreo. In a nutshell, if an app is targeting Oreo and your phone is running Android 8.0 or higher, it can't run unchecked in the background anymore.When you're actively using an app, it's considered to be running in the foreground. In this situation and a few other rare cases, the app can run any operations it wants — after all, you're using the app, so the services it's running are inherently tasks the user authorized it to perform.When you're not using an app that targets Oreo, Android 8.0 and newer builds will consider it to be running in the background. Once it's moved to the background, the system will give the app a few minutes to wrap up any processes it was running, but after that, Android will terminate all of the app's processes.For malware apps, this means they can no longer keep active data connections in the background to "phone home," nor can they run services indefinitely to monitor your activity and collect information on you. This will severely limit some of the shadiest behavior in Android malware apps.Of course, developers of existing malware apps could simply not update their apps to avoid having to comply with these new rules. However, outdated apps generally rank lower on Play Store search results than their updated counterparts, so fewer users will come across them in the first place. And at the very least, there are several new hurdles for any shady developer looking to upload a new malware app.Overall, these new rules mark a huge shift in the Android ecosystem. Their impact stretches far beyond malware — folks running newer Android versions should see lots of other benefits, like better battery life, split-screen support, more apps that work with taller screens, and even improved camera quality.Don't Miss: Why Snapchat STILL Doesn't Take Great Pictures on AndroidFollow Gadget Hacks on Pinterest, Reddit, Twitter, YouTube, and Flipboard Sign up for Gadget Hacks' daily newsletter or weekly Android and iOS updates Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image and screenshots by Dallas Thomas/Gadget Hacks
Inspect Google form for action attribute. a. Copy the same action to your form. Inspect and find values for attributes name in the Google form. a. Give the same name values for your form items as well. The values look like entry.742532386. Check if your form gets the responses. Since it is a native
0 comments:
Post a Comment